How frequently are websites scanned?
We scan websites every business day (Monday-Friday).
What are some of the websites from which you remove information?
The websites where we most frequently find information are Nuwber, Spokeo, Yellow Pages, USA Profile Pages, Radaris and Intelius. We also conduct broader searches of police officers, law enforcement personnel and their family members to identify new sites posting information, such as social media and individually created websites. Once we find those sites, they are added to our list for daily searches.
How frequently do you provide privacy status reports?
Privacy status reports are updated in real-time and available 24/7 via a custom and secure online portal. Most users receive three to four updates per week with multiple listings.
How do police officers enter their personal information and stay updated on any outstanding issues?
Police officers can log in to the secure portal 24/7 to review their account. Below is a screenshot of how the system tracks both outstanding and resolved privacy issues.
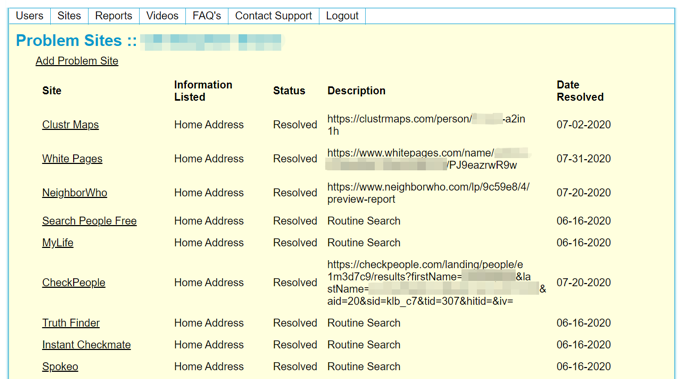
How can police officers register for the service?
Police officers are able to register for the service either by using the secure form here. If you are a part of an organization or association and would like to discuss pricing, please contact us directly. You can contact us for live support to help them with the process Monday-Friday, 8:00 a.m.-5:00 p.m.
How can a police officer contact your company to receive further knowledge about information found online?
Once they have registered for the service, police officers receive an onboarding email that includes contact information to call or email our team directly.
There is also a “Contact Support” button on the portal. The subject dropdown options are “General Inquiry” and “Sites of Concern.” Those messages are sent to us via email, and we reply to them within two hours on the same day, Monday-Friday.
What are your customer support hours?
If police officers have questions about their notifications, live customer service is available via a toll-free number or email from 8:00 AM - 5:00 PM, Monday-Friday.
How do you safeguard the personal information of police officers once it is received in your system? What types of physical and cybersecurity measures do you utilize?
Security is paramount to our process.
We employ numerous techniques to safeguard the information we gather, starting from the moment we request that information.
Our procedures and safeguards include:
- Our automated system flags issues and provides a summary report of issues to a human reviewer. The human reviewer can also access the accounts assigned to him/her for review and all access attempts are logged in the system for auditing purposes to flag suspicious, after hours or unauthorized attempts at viewing information.
- Most of the searches only require a name to show to the human reviewer to verify; if additional information (such as an address) is needed, the human reviewer must click on each individual piece of information and enter his or her password to see the information. Each attempt is logged in the database.
- Social security numbers are not collected or stored.
- If a request originating from a public IP attempts to access more than one account, the information is logged and an automated alert is sent to our 24-hour security team. They investigate within five minutes, and if there is suspicious activity the server is taken offline until a reason or intrusion can be found. All IP addresses and login attempts are recorded and monitored.
- Officers can view their information, and that of their families, but multiple failed attempts at a login, or trying to log in to another officer’s account from the same IP address, triggers a security alert.
- Security access patterns are analyzed monthly or when a suspicious alert is created, whichever comes first.
- We have proprietary intruder detection protocols that we do not advertise, but which alert us of intrusions. The goal in our architecture is not only to avoid intrusion, but also to delay and segregate so that intrusions can be detected and stopped. Breaching one level of security only gains access to small amounts of information (or even to just one individual’s portal view). System-wide reviews from outside IPs are not allowed.
- We do not barter, sell, trade or otherwise use your information with any outside source. Your information belongs to you. At any point, you can ask us to delete your information and close your account. If you deactivate your account, we will keep it dormant for 90 days. After 90 days, we will delete your information.
What types of background checks do you utilize for your employees?
Employees who have physical access to servers, have accounts for searches or serve as security personnel are required to undergo the following security checks:
- A pre-employment background check for felonies, arrests, discharge from previous employers for moral charges, theft, or drug arrests.
- An annual online check for any recent criminal or drug-related activities.
Ready to get started?
Have additional questions? Contact us, where here to help.
